If you use discord, You’ve probably encountered someone who has either shared on a server or Sent you some malicious link, Weird Pornographic videos or animal abuse videos.
These are things that are most commonly found in small discord servers which are either based on hacking or gaming.
While I try to stay away from these places, I have found a couple of users trying to spread around their cute “discord token grabbing” malware. They are everywhere. EVERYWHERE! Can’t escape them! Most likely you have also seen them.
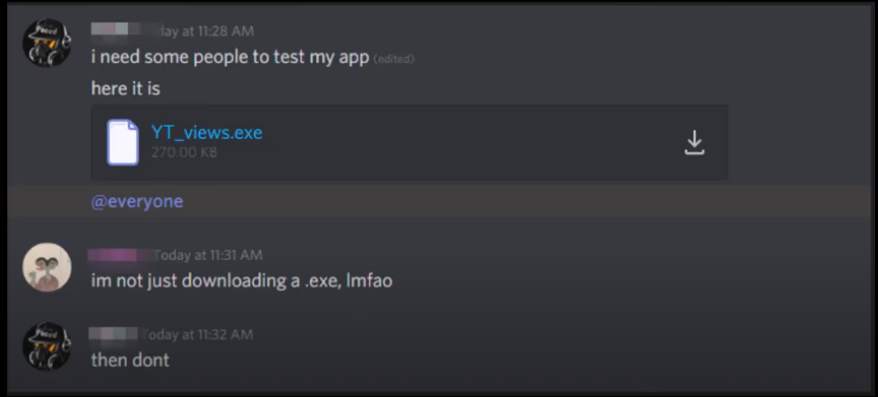
here is a screenshot of what me and my buddy August found on a random server.
The user is sharing a Discord token grabber malware.
Here is what I found in a server I’m in on discord.
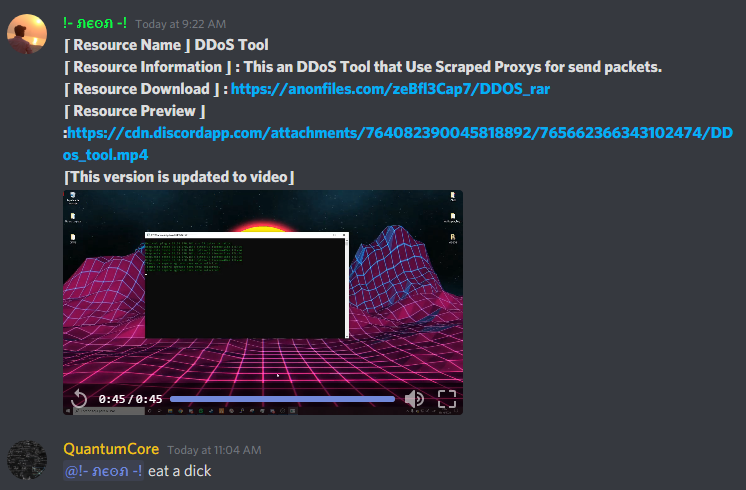
- Anon files link.
- According to the video, It’s a DDOS program that uses cmd ping. ._.
- It does not have any proxy.
The instant I saw this I forwarded to August who reversed it, And indeed, It’s also a Discord token grabber.
Token Location: z **Token**Fz
icon_url
textz
Token grabber by )
color
fields
author
footer
Mamberroiz^https://cdn.discordapp.com/attachments/762279569922588692/802323830839836692/foto_de_nadie.png)
content
embedsrd
avatar_urlzxhttps://discord.com/api/webhooks/801924788821557258/jthf_q6_keBpHhZj90mNGaxhl-r3WCCfsUTo_XLCTgjBhJuAItFZ9UddBQ7td3jln0PB)
utf-8) gettokens%
wodxz!https://pastebin.com/raw/UttzUj96)
devr
getdeveloper0
Nonez
https://api.ipify.org)
getip7
Nz#https://cdn.discordapp.com/avatars/
.gif
urlr
getavatar>
wmic csproduct get uuidT)
shell
stdin
stdout
stderr
split)
gethwidE
Nz5https://discordapp.com/api/v6/users/@me/relationshipsr
getfriendsH
Nz0https://discordapp.com/api/v6/users/@me/channels
recipient_id
data
encoder
getchatM
Nz?https://discordapp.com/api/v6/users/@me/billing/payment-sourcesr
bool
lenr
has_payment_methodsR
Nz'https://discordapp.com/api/v6/channels/z /messageszWmultipart/form-data; boundary=---------------------------325414537030329320151394843687rO
chat_id
form_datar
send_messageW
Exceptionrdelay
friendrW
spread\
sxq`t
d$d%|
d+d,d-
d0d1
t t!|
)7Nz \.cache~$T
UserName
COMPUTERNAME
userprofiler)
mfa.
username
discriminatorrQ
avatar
email
phone
premium_typeiThe strings above are taken from the Executable file itself. It contains a pastebin link, Which is a username to which I assume is the person responsible for this.
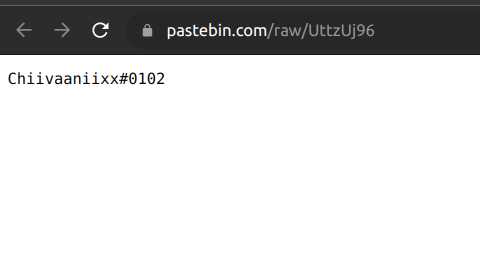
I mean you made this site in WordPress, anyone’d take you with a grain of salt.
yep
Hi there Dear, are you genuinely visiting this site daily, if so afterward you will without doubt take fastidious
know-how.