Distributing Executables that contain the entire functionality of the Client is dangerous. It will be blocked by anti viruses and there is no stealth in it whatsoever.
Introducing the new Reflective Loader Client.
The Reflective Loader Client is a small lightweight program that establishes connection to RHP Server then waits for you to send it a Payload to Execute, In memory. The Payload being a Reflective DLL.
The Reflective Loader Client can be used to run the Probe directly from memory, Here’s how it looks like.
Once the Reflective Loader is executed in the Client machine, It will connect back and wait for you to send it a Payload.
It will appear under the Reflective Loader Handler Tab in RHP V.2+.
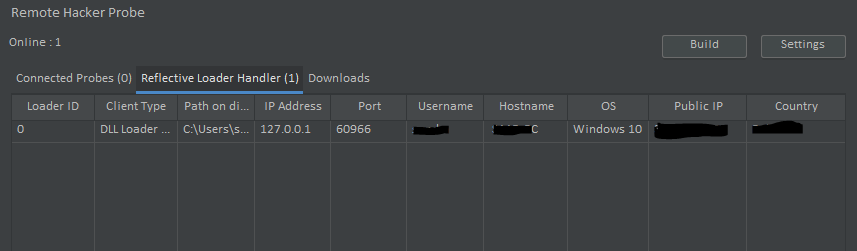
At this point the Reflective Loader is in, Kind of a sleep mode. It is and will do nothing but stay connected until you send it a Payload.
So lets load the Probe Client from Memory.
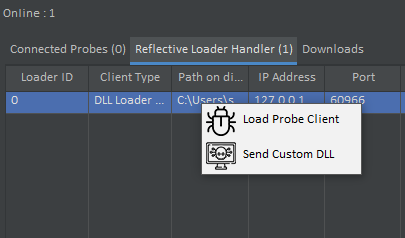
“Load Probe Client” sends the Reflective Probe Payload, Which is executed with Server Host and Port as arguments.
Once Executed, The Reflective Loader will disconnect, And after 5 seconds. A Probe should connect with the Client Type of “Reflective Probe”. This means that the Probe is running from memory rather than the normal “Probe Client” which is run from disk.
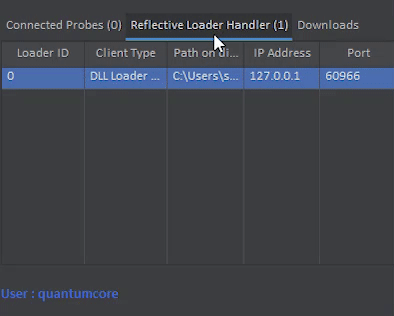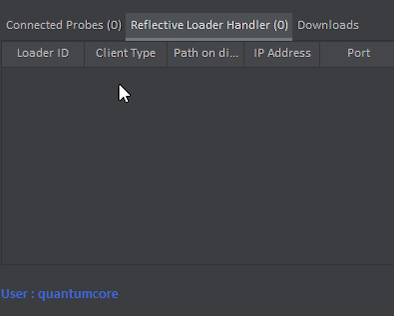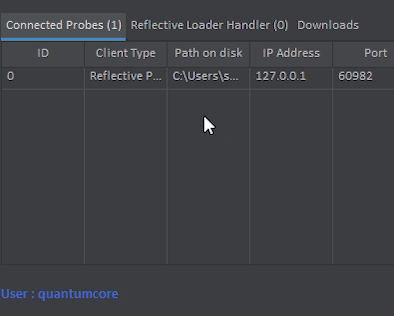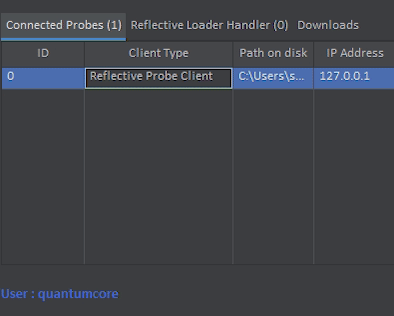
The default process that is injected into is it self, However, This can be changed. You can even migrate to other processes now.
The main advantage of this feature is evading anti viruses, You can even load Meterpreter from Reflective Loader Client without getting detected.
This feature is still in development, The expected goal is to be able to load any payload, Even built in RHP Payloads from reflective loader.